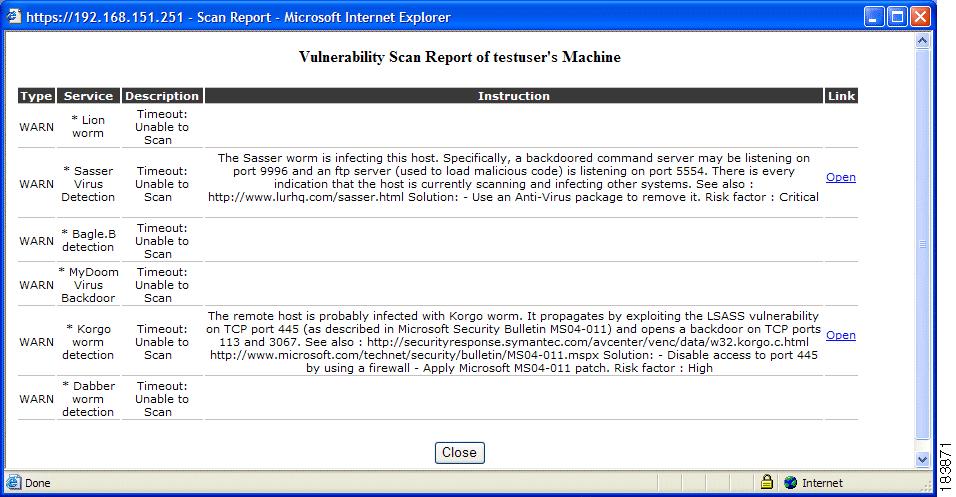
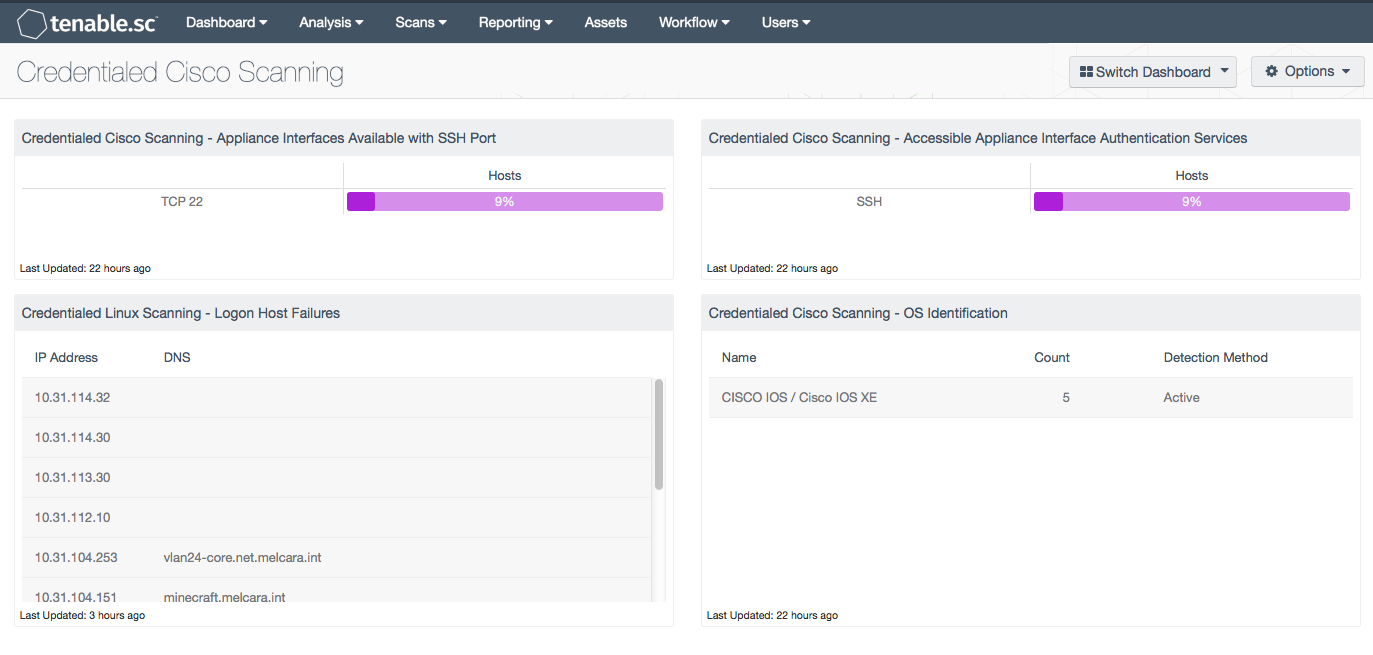
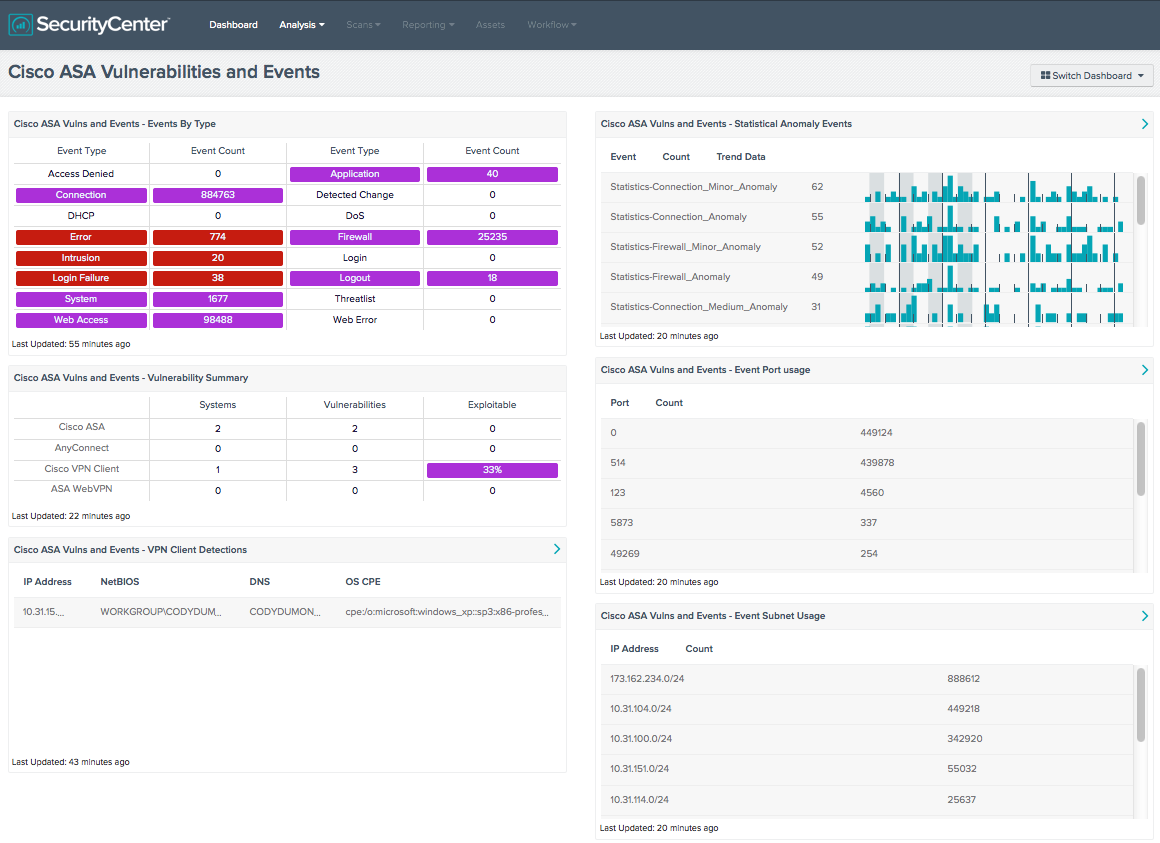
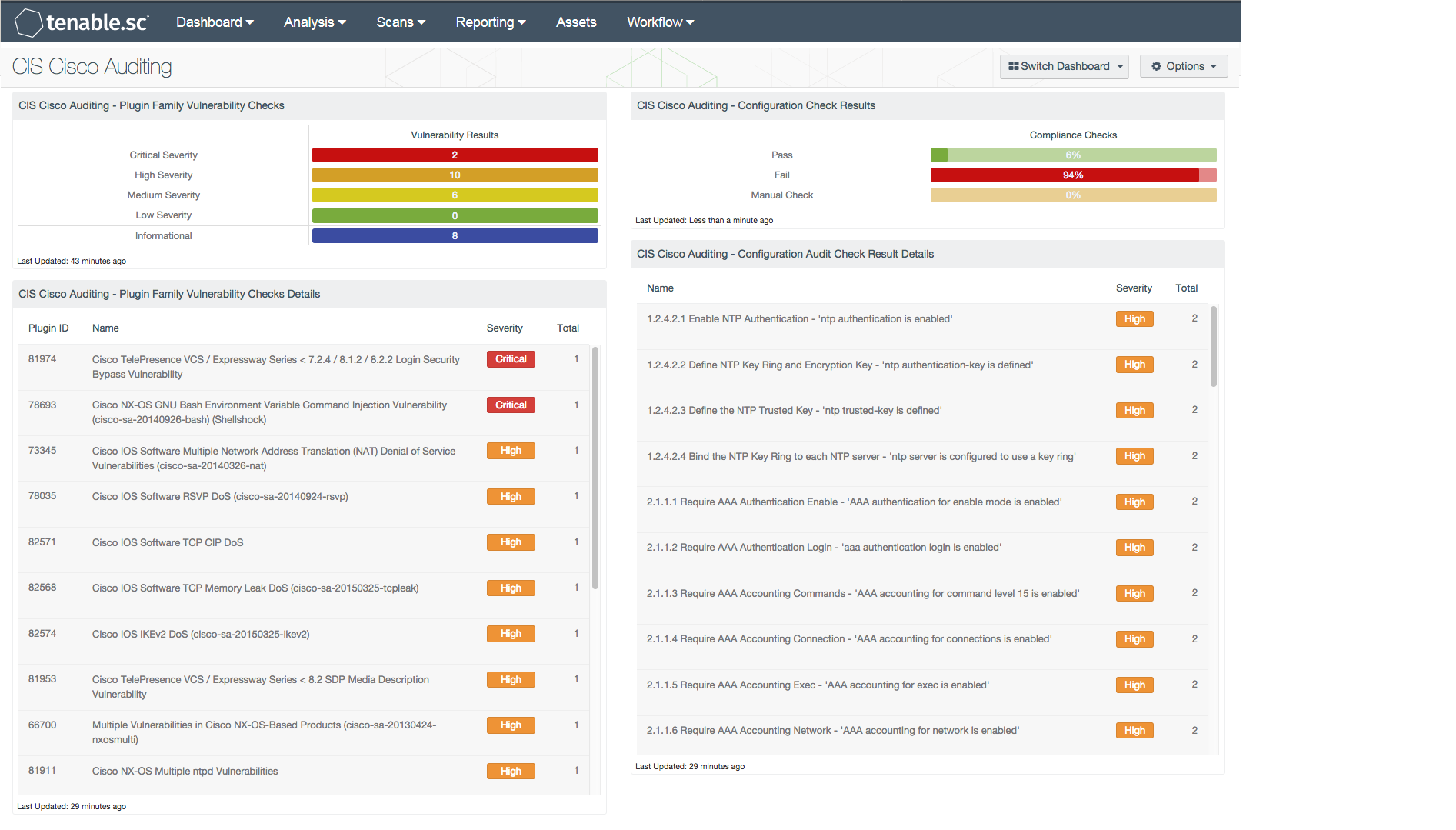
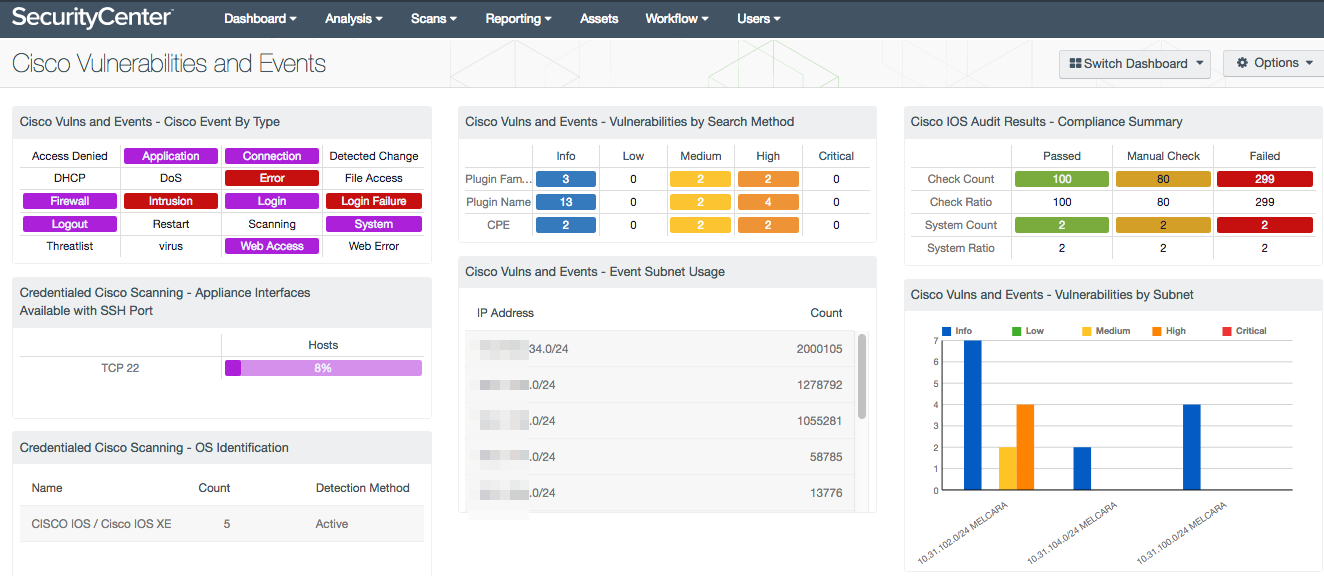
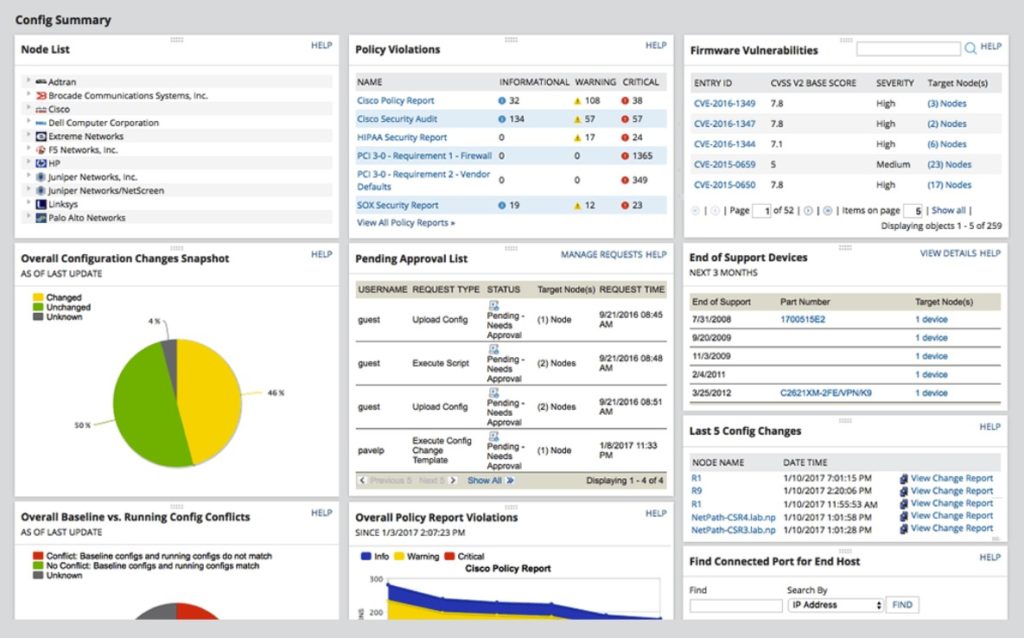
Cisco Cybersecurity Essentials 3.3.1.9 Detecting Threats and Vulnerabilities | Linux demonstration - YouTube

CVE-2020-3452: Cisco Adaptive Security Appliance and Firepower Threat Defense Path Traversal Vulnerability - Blog | Tenable®

Asset Inventory for Internal Network: problems with Active Scanning and advantages of Splunk | Alexander V. Leonov