![PDF] REGULATING THE AUDIT QUALITY AND DEPROFESSIONALISATION OF THE AUDITING PROFESSION | Semantic Scholar PDF] REGULATING THE AUDIT QUALITY AND DEPROFESSIONALISATION OF THE AUDITING PROFESSION | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ec2d44130680b260481c3784a095248d3eef038b/6-Table1-1.png)
PDF] REGULATING THE AUDIT QUALITY AND DEPROFESSIONALISATION OF THE AUDITING PROFESSION | Semantic Scholar

Accounting Information Systems, 5 th edition James A. Hall COPYRIGHT © 2007 Thomson South-Western, a part of The Thomson Corporation. Thomson, the Star. - ppt download

Explaining the (non-) adoption of advanced data analytics in auditing: A process theory - ScienceDirect

Solved: Chapter 14 Problem 1RQ Solution | Accounting Information Systems & Qkbks 2011 11th Edition | Chegg.com

PDF) The Business Risk Audit Approach in Less Developed Countries: Modernisation and Reality of Audit Practice











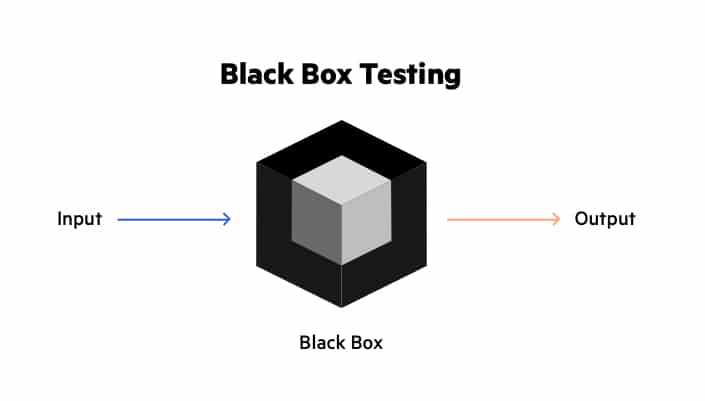
![Different forms of Black Box Testing [3] | Download Scientific Diagram Different forms of Black Box Testing [3] | Download Scientific Diagram](https://www.researchgate.net/profile/Fazlullah-Khan-2/publication/303280520/figure/fig1/AS:376806143217664@1466848993069/Different-forms-of-Black-Box-Testing-3.png)